Companies made more than $2.1 billion in payments to ransomware gangs from January 2022 to December 2024, a U.S. government report revealed.
The Treasury Department’s Financial Crimes Enforcement Network (FinCEN) released a study last week covering 4,194 ransomware incidents that were reported through the Bank Secrecy Act over the three-year period.
The department noted that the figures from the three-year stretch nearly outpaced all of the reports and ransomware payments from the previous nine-year period of 2013 to 2021 — where they received 3,075 reports and saw approximately $2.4 billion in ransomware payments.
The report found that ransomware payments reached an all time high in 2023 with about $1.1 billion making its way into the hands of hackers — a 77% increase compared to 2022.
Of the 267 ransomware gangs tracked by the department, the ALPHV/BlackCat group was the most prevalent alongside Akira, LockBit, Black Basta and Phobos.
The report noted that following the law enforcement takedowns of ALPHV and LockBit, there were noticeable decreases in ransomware incidents in 2024. After seeing 1,512 incidents in 2023, there were 1,476 reported in 2024 that led to about $734 million in payments.
Throughout the report, 2023 stood out as a particularly damaging year for companies. The median ransomware payment peaked in 2023 at $174,000 — significantly more than the $124,097 in 2022 and $155,257 in 2024.
Ransomware gangs targeted financial services firms, manufacturing companies and the healthcare industry the most, according to the report.
About 97% of payments were made in Bitcoin, the Treasury Department noted, adding that most gangs used unregulated cryptocurrency exchanges to launder the funds. The report also tied different ransomware gangs to several of the same initial access vendors.
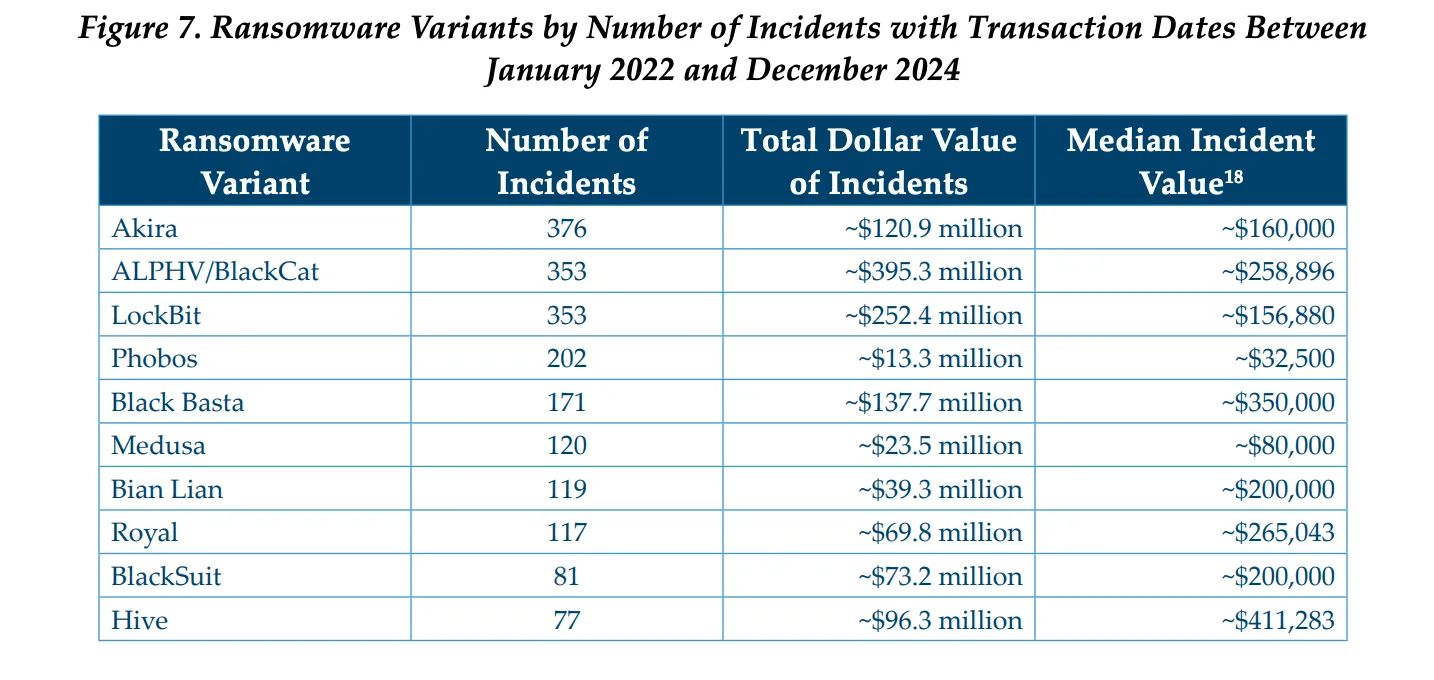
Image: FinCEN
The 10 ransomware variants with the highest cumulative payments accounted for $1.5 billion over the 2022-2024 period.
While ALPHV earned nearly $400 million in ransom payments, LockBit saw a ransom total of $252.4 million and Black Basta brought in $137.7 million. Hive, which had $96.3 million in earnings, had the highest median incident value of $411,283.
Akira was responsible for the largest number of ransomware reports at 376, followed by ALPHV and LocKBit which each accounted for 353 incidents.
The report also covers the ways ransomware gangs communicated with companies and noted that several gangs made further financial demands even after receiving initial ransom payments.
The findings add context to the constantly evolving ransomware ecosystem, which gained national prominence following the 2021 Colonial Pipeline attack that had real world impacts on thousands of people across the East Coast of the U.S.
Since then, several ransomware incidents have caused chaos around the world, including attacks on major companies like UnitedHealth, the Industrial and Commercial Bank of China and Synnovis as well as the governments of Dallas, Oakland, Costa Rica, Albania, Bermuda and others.
The U.S. led the creation of the International Counter Ransomware Task Force in 2023 that involved dozens of countries but the effort has had mixed success because most ransomware gangs are based in Russia or other countries that will not extradite their citizens.
Recorded Future
Intelligence Cloud.
No previous article
No new articles
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.












