Recent reports have highlighted a concerning development – a persistent and sophisticated cyber-espionage campaign carried out by the Chinese hacker group TAG-74. Over the course of several years, TAG-74 has been systematically targeting South Korean organizations, raising alarms in both the cybersecurity community and diplomatic circles. In this article, we delve into the details of this campaign, its potential implications, and the importance of bolstering cybersecurity measures.
The TAG-74 Campaign Unveiled: TAG-74, a suspected state-sponsored Chinese hacker group, has earned notoriety for its cyber-espionage activities. Recent findings suggest that this group has been conducting a sustained campaign against South Korean entities, which are no strangers to cyber threats given their geopolitical significance.
Key Campaign Elements:
- Advanced Persistent Threat (APT): TAG-74’s tactics are reminiscent of an APT group. Their attacks are highly targeted, sophisticated, and often span extended periods, making them difficult to detect.
- Supply Chain Attacks: The group is known for infiltrating the supply chain of its targets, compromising trusted software vendors or service providers to gain access to their intended victims.
- Zero-Day Exploits: TAG-74 leverages zero-day vulnerabilities in popular software applications to maintain access and exfiltrate sensitive data without detection.
- Information Gathering: The hackers employ various techniques, including spear-phishing emails and watering hole attacks, to gather valuable intelligence about their targets.
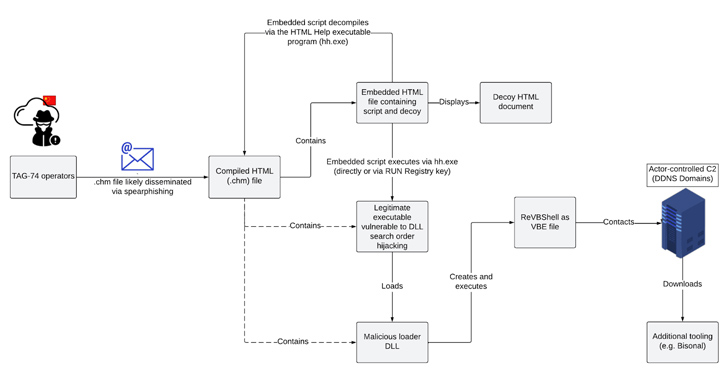
Implications for South Korean Organizations: The repercussions of TAG-74’s campaign extend beyond mere data breaches. Potential consequences for South Korean organizations include:
- Economic Espionage: Stealing proprietary data and intellectual property could provide China with a competitive edge in economic sectors where South Korea excels, such as technology and manufacturing.
- National Security Concerns: If TAG-74 gains access to sensitive government systems or military-related information, it could pose a significant threat to South Korea’s national security.
- Diplomatic Tensions: Such cyber-espionage activities can strain diplomatic relations between countries, potentially leading to diplomatic crises.
Bolstering Cybersecurity Measures: In the face of persistent threats like TAG-74, South Korean organizations must prioritize cybersecurity measures to protect their assets. This includes:
- Advanced Threat Detection: Implementing robust threat detection systems to identify and respond to APTs like TAG-74 in real-time.
- Security Awareness: Conducting regular cybersecurity training and awareness programs to educate employees about phishing and other social engineering tactics.
- Patch Management: Promptly applying security patches and updates to eliminate known vulnerabilities.
- Multi-Factor Authentication (MFA): Enforcing MFA to enhance login security and reduce the risk of unauthorized access.
- Collaboration: Cooperating with international partners and sharing threat intelligence to collectively combat cyber threats.
Conclusion: TAG-74’s multi-year campaign against South Korean organizations underscores the persistent and evolving nature of cyber threats. It serves as a stark reminder that cybersecurity is a global concern, requiring vigilance, collaboration, and proactive measures to protect critical assets. South Korean entities, along with the broader global community, must remain committed to enhancing their cybersecurity posture to mitigate such threats effectively.










